
Dr. Antje Winkler
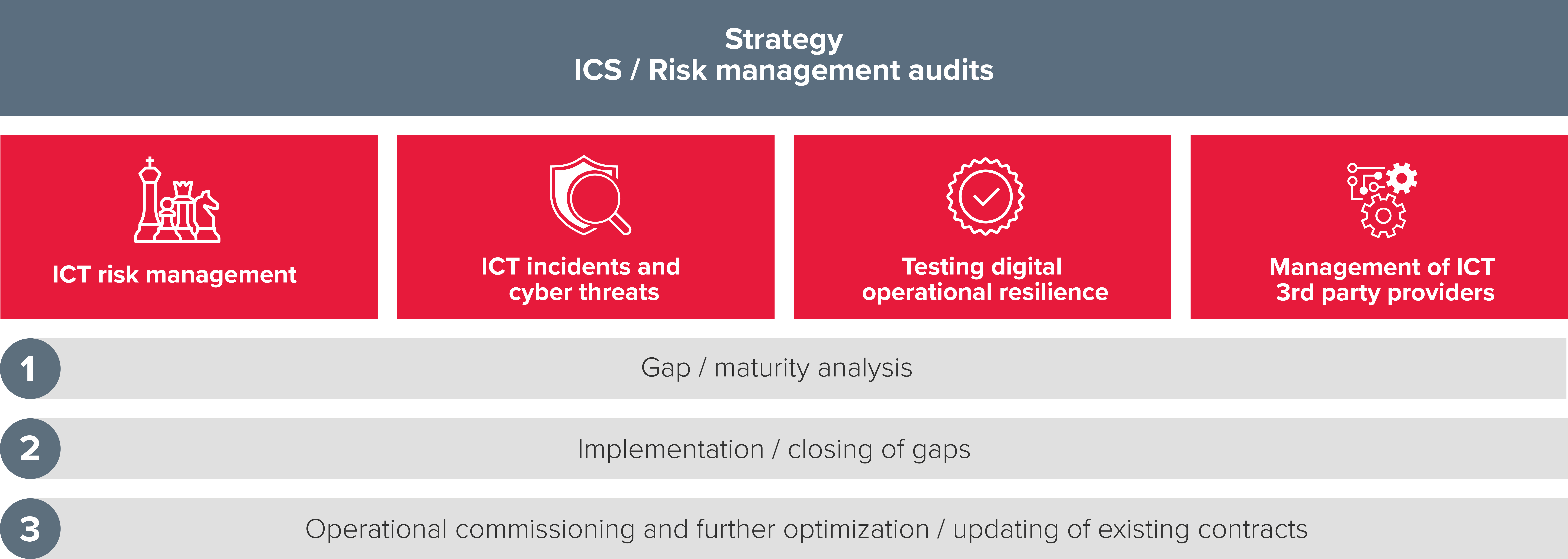
Financial organisations must develop and implement a comprehensive ICT risk management framework that is tailored to their size, complexity and risk profiles. This framework must ensure that risks associated with ICT systems are identified, assessed, mitigated and (continuously) monitored.
Another important aspect of DORA is the compliance/ managing of ICT disruptions and cyber threats. Financial organisations must be able to respond quickly and effectively to security incidents. To this end, institutions must ensure that they have the necessary resources to successfully fend off cyber-attacks and minimise the impact of incidents in the best possible way.
DORA requires financial organisations and third-party ICT service providers to regularly test the digital operational resilience of their relevant applications and systems once a year. This includes a variety of test scenarios, including stress tests and penetration tests.
Penetration tests are an extremely effective tool for uncovering potential security gaps, identifying remedial measures, and thus increasing the level of security. Through regular penetration tests, companies can actively combat threats and better protect their data and business processes.
To best prepare for an emergency and improve resilience in the long term, DORA also stipulates the regular performance of Threat-Led Penetration Tests (TLPT) in accordance with Threat Intelligence-based Ethical Red Teaming (TIBER DE/EU) for financial organisations of particular importance to financial stability. This involves a targeted review of established security mechanisms to identify potential for optimising cyber defence measures.
Companies must develop more comprehensive processes for monitoring and managing the risks posed by ICT service providers. In addition to extended minimum contract standards, due diligence must be carried out when selecting service providers and all ICT risks associated with the procurement of services must be identified and assessed. Based on the ICT risks, it must also be determined whether a third-party ICT service provider is involved in supporting critical or important functions for which extended requirements (e.g. sufficient resilience and coordinated emergency plans) apply.